With the release of image scanning using Microsoft Defender for container registries, we received enormous interest in findings among wide audiences including traditional Microsoft Defender for Cloud admins along with repository owners and DevOps personnel.
One of the biggest challenges that was raised by these audiences was how to use the Defender for Container scanning capability in their integration and deployment processes to ensure only scanned and healthy images reach the production environments.
By embedding Microsoft Defender for container registries assessments into your CI/CD pipeline, you can address this need and have a more secure automation and deployment processes in enterprise environments.
In this article, what we will be doing is as follows:
- Create an Azure Resources Group (AZRG)
- Create an Azure Container Register inside the AZRG above
- Enable Azure Defender for Container
- Create a vulnerable Docker Image
- Setup the CICD Pipeline in the Github Action
- Verify and review vulnerability assessment results.
Required: You need basic knowledge of Azure Security Center, Azure CLI, Azure DevOps toolchains.
Overview
our article follows this diagram:
Okay, let's do it:
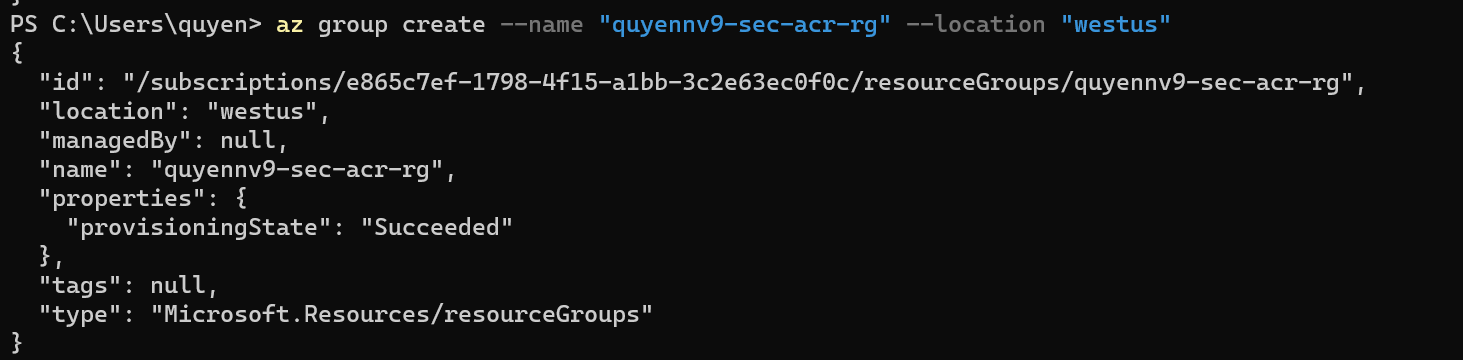
Step 1: Create the AZRG
az group create --name "quyennv9-sec-acr-rg" --location "westus"
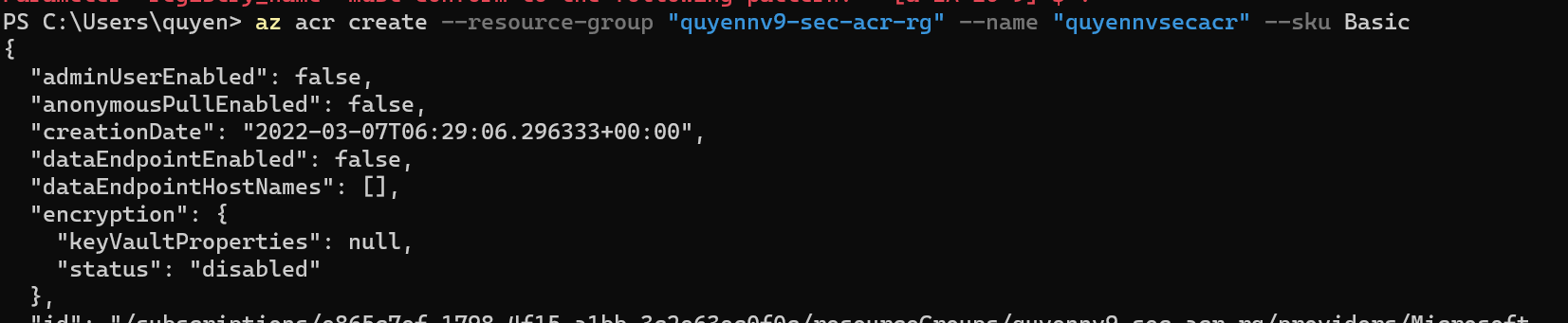
Step2: Create the ACR
az acr create --resource-group "quyennv9-sec-acr-rg" --name "quyennvsecacr" --sku Basic
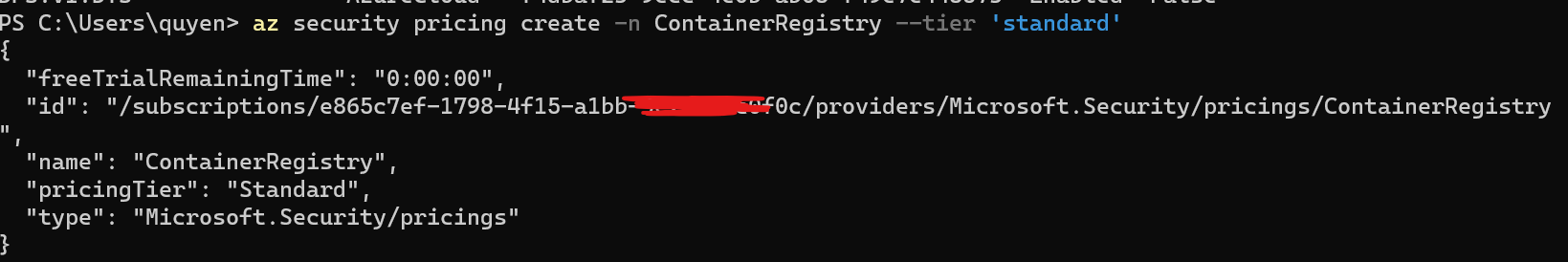
Step 3: Enable Azure Defender for Container
az security pricing create -n ContainerRegistry --tier 'standard'
Step 4: Create Vulnerable docker container
FROM ubuntu:18.04
ARG firefox_version="88.0.1"
RUN apt-get update \
&& apt-get install -y wget \
&& rm -rf /var/lob/apt/lists/*
## Install Firefox 88.0.1
RUN apt-get purge firefox \
&& apt-get purge firefox \
&& apt-get install libgtk-3-0 -y \
&& apt-get install libx11-xcb1 -y \
&& apt-get install libdbus-glib-1-2 -y \
&& apt-get install libxt6 -y \
&& wget http://ftp.mozilla.org/pub/firefox/releases/${firefox_version}/linux-$(uname -m)/en-US/firefox-${firefox_version}.tar.bz2 \
&& tar xvf firefox-${firefox_version}.tar.bz2 \
&& mv firefox /opt/ \
&& ln -s /opt/firefox/firefox /usr/bin/firefox
CMD ["bash"]
Step 5: Setup the CICD Pipeline in the Github Action
Create 4 repositories secret bellow for the pipeline
- ACR_USERNAME
- ACR_PASSWORD
- ASC_AUTH_TOKEN
- ASC_NAME
with ASC_NAME and ASC_AUTH_TOKEN (ASC is Azure Security Center, today is Microsoft Defender for Cloud).
you go to, MDC . go to settings and Integrations
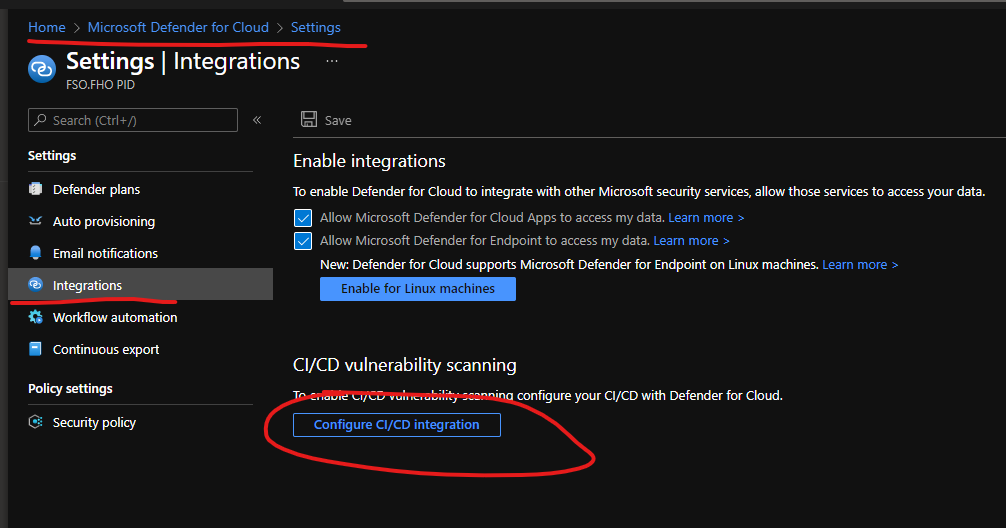
Now, we create a single job that does the following details steps:
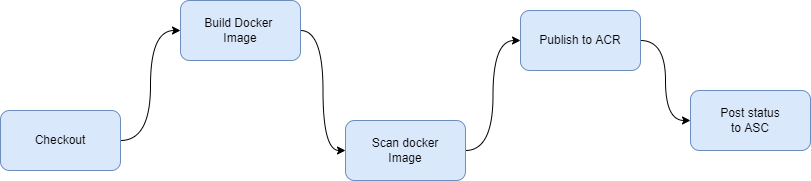
Here is the pipeline file you'd need for the project
Link: https://raw.githubusercontent.com/quyennguyenvan/acr-secure-scan/main/.github/workflows/main.yml
# This is a basic workflow to help you get started with Actions
name: Sample workflow to scan image and publish to Azure Container Registry
# Controls when the workflow will run
on:
# Triggers the workflow on push or pull request events but only for the master branch
push:
branches: [main]
pull_request:
branches: [main]
jobs:
asc_scan:
runs-on: ubuntu-latest
env:
ACR_REPO_NAME: scan-vul
ACR_SERVER: quyennvsecacr.azurecr.io
steps:
- name: Checkout sample Dockerfile
uses: actions/[email protected]
with:
ref: 'main'
- name: Build a Docker image
run: |
docker build -t ${{ env.ACR_SERVER }}/${{ env.ACR_REPO_NAME }}:${{ github.sha }} --file vul-docker.dockerfile .
- name: Scan Docker image using Azure Container Scan action
uses: Azure/container-scan@v0
id: container-scan
continue-on-error: true
with:
image-name: ${{ env.ACR_SERVER }}/${{ env.ACR_REPO_NAME }}:${{ github.sha }}
# run-quality-checks provides CIS benchmark assessment
run-quality-checks: true
- name: Login to Azure Container Registry
uses: Azure/docker-login@v1
with:
login-server: quyennvsecacr.azurecr.io
username: ${{ secrets.ACR_USERNAME }}
password: ${{ secrets.ACR_PASSWORD }}
- name: Push scanned image to ${{ env.ACR_REPO_NAME }}
run: |
docker push ${{ env.ACR_SERVER }}/${{ env.ACR_REPO_NAME }}:${{ github.sha }}
- name: Post result status to Azure Security Center
uses: Azure/publish-security-assessments@v0
with:
artifact-type: containerImage
scan-provider: trivy
connection-string: ${{ secrets.ASC_NAME }}
subscription-token: ${{ secrets.ASC_AUTH_TOKEN }}
# Do not modify ${{ steps.container-scan.outputs.scan-report-path }} as it uses this path by default in Version 0.1
scan-results-path: ${{ steps.container-scan.outputs.scan-report-path }}
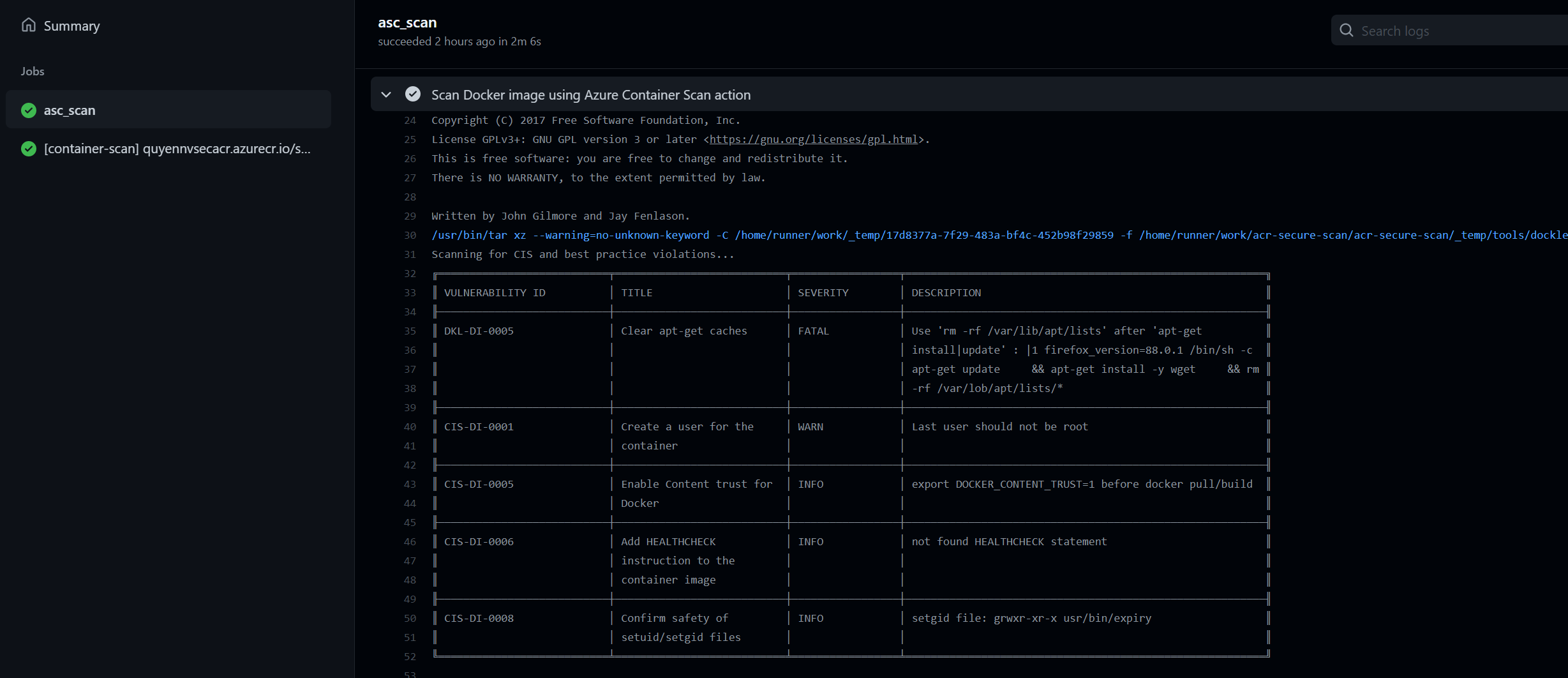
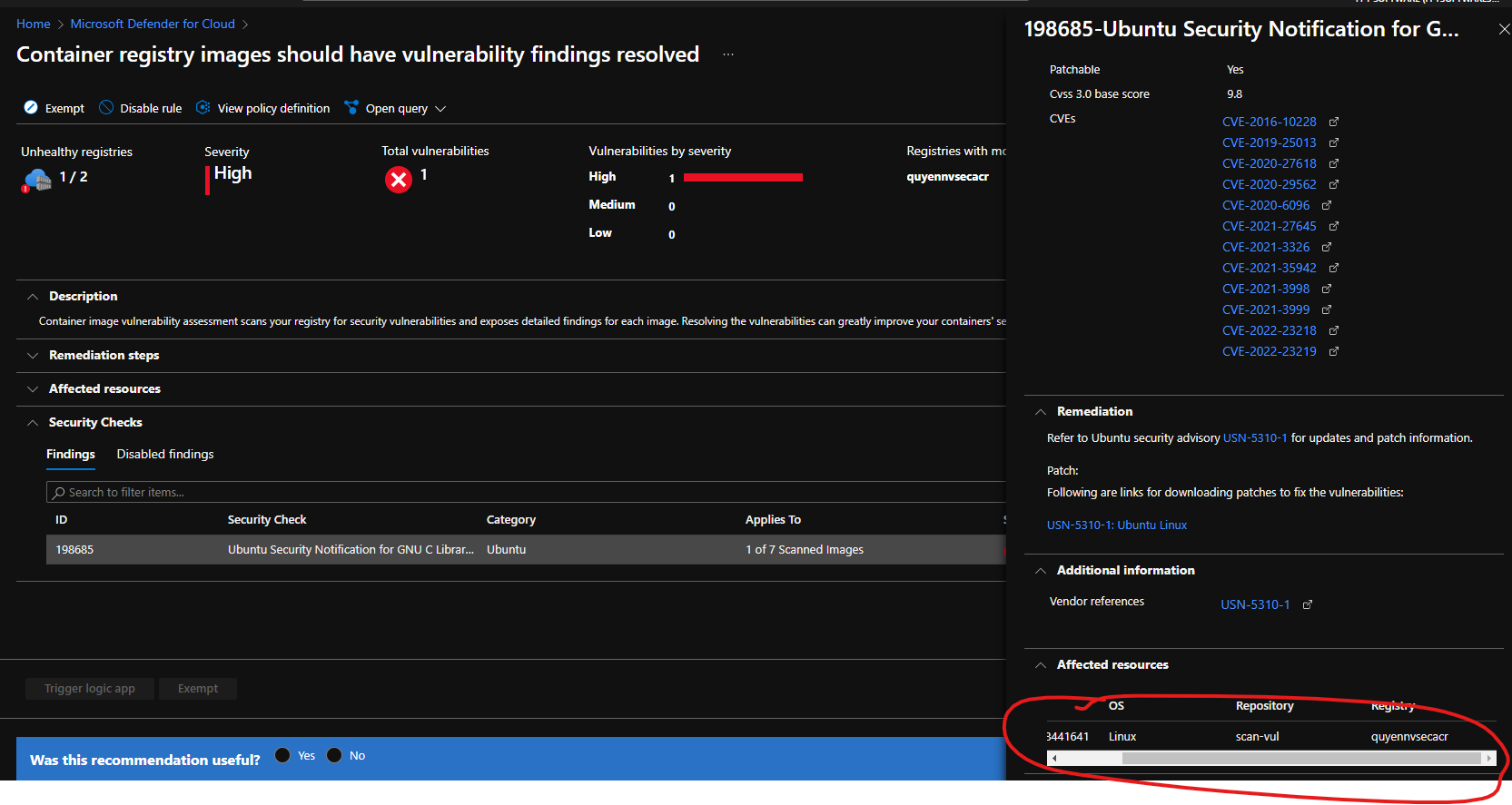
Step 6: Verify and review vulnerability assessment results
now you go to the MDC > Recommendations. Search for Container registry images should have vulnerability findings resolved.
Resources: quyennguyenvan/acr-secure-scan (github.com)



